Adopting sensitivity labels to drive data security in the era of Microsoft Copilot
Organizations can invest in the best data protection technologies, but their effectiveness depends entirely on how well employees apply them. Microsoft Purview Sensitivity Labels provide powerful tools to classify, protect, and govern data, but if users don’t understand when or how to apply them, even the best labeling strategy fails to prevent data leaks or enforce compliance.
A strong adoption strategy ensures that sensitivity labels are integrated into daily workflows and that users see them as an enabler rather than an obstacle. Successful adoption requires a structured approach; starting with a focused rollout, gradually expanding to more teams and use cases, and reinforcing best practices through targeted training and automation.
This blog explains and inspires how to approach sensitivity label adoption strategically, ensuring that a well-defined labeling strategy is in place and that labels are applied consistently, correctly, and efficiently across the organization.
Using the ADKAR Model to Drive Adoption
The ADKAR model by PROSCI is a widely used framework for managing organizational change. It provides a structured approach to ensure that users not only understand the need for sensitivity labels but also adopt them as part of their daily workflows. The five key stages of ADKAR are:
- Awareness – Communicate why sensitivity labels matter (data protection, compliance, risk prevention). Conduct targeted awareness campaigns, such as email updates and internal webinars.
- Desire – Align labeling with business goals so employees see it as useful, not burdensome. Highlight real-world examples where sensitivity labels prevented data loss or compliance violations.
- Knowledge – Provide training, guides, and tooltips to ensure users understand how to apply labels correctly. Use knowledge checks and quizzes to reinforce understanding.
- Ability – Reinforce real-world application through automation, easy-to-use tools, and ongoing coaching. Implement mentorship programs where experienced users help new adopters.
- Reinforcement – Monitor label usage, provide feedback, and continuously improve classification strategies. Reward teams with recognition programs for consistent and correct labeling practices.
By applying the ADKAR model, organizations can systematically guide users through each stage of change, ensuring that sensitivity labels become a well-adopted security control rather than an ignored compliance requirement.
Where to Start: Small and Focused or Organization-Wide?
One of the most common questions when rolling out sensitivity labels is: Should we start small or implement them across the organization all at once? The answer depends on the organization’s size, complexity, and maturity in data classification.
Option 1: Start Small with a Pilot Group
For organizations new to sensitivity labeling, starting with a pilot group can reduce risk and allow for testing before full deployment.
-
Select a specific department or business unit that frequently handles sensitive information (e.g., Finance, HR, or Legal).
-
Define a limited set of sensitivity labels that address common security concerns but avoid unnecessary complexity.
-
Monitor how the pilot group interacts with the labels, reviewing progress on a biweekly basis and documenting key insights in a structured report. Track trends such as common misclassification issues, user adoption rates, and feedback from pilot users to iteratively refine the labeling strategy.
-
Use feedback sessions and surveys to identify user challenges and refine training materials before expanding.
Option 2: Start Small with a Limited Set of Labels
Even if rolling out organization-wide, keeping the initial set of labels simple ensures easier adoption.
- Instead of introducing too many labels at once, start with three to five broad labels that cover common scenarios(e.g., Public, Internal, Confidential, Restricted).
- Once users become comfortable, expand to department-specific labels (e.g., HR Confidential, Legal Privileged).
- Establish clear guidelines on when to use each label, using practical examples in training materials.
- Avoid overcomplicating the classification process—too many labels lead to confusion and inconsistent application.
Key Considerations for a Successful Adoption Strategy
1. Make Labeling Easy for Users
Users will resist any process that adds extra complexity to their workflows. To encourage adoption:
-
Use automatic labeling where possible to reduce manual effort.
-
Apply common labels, which are predefined by IT and security teams based on common data classification needs. While users always have to choose a label, defining a default label for common document types can streamline the process and reduce decision fatigue. These labels, such as ‘Public,’ ‘Internal Use Only,’ ‘Confidential,’ and ‘Highly Confidential,’ help streamline the classification process, reduce errors, and ensure consistency across the organization.
-
Ensure labels integrate seamlessly into Microsoft 365 apps (Outlook, Word, Excel, Teams, SharePoint) through Microsoft Purview, enabling consistent enforcement of data protection policies across all platforms.
-
Provide tooltips and inline guidance that offer clear and contextual instructions, such as ‘Use the Confidential label for internal financial reports’ or ‘Highly Confidential labels should be applied to documents containing personal data.’
-
Implement default labels for common document types, reducing decision-making friction for users.

2. Train and Educate Employees
Training is a critical part of adoption and should align with the ADKAR model to ensure employees not only understand sensitivity labels but also actively use them. This can be achieved through:
-
Targeted workshops where users receive hands-on experience applying labels to real business documents.
-
Department-specific training sessions, making labeling relevant to users’ daily work.
-
Structured learning programs within Microsoft 365, leveraging in-app tutorials and guided task-based learning modules.
-
Live office hours and coaching sessions where employees can ask questions and receive real-time feedback.
-
Gamification and incentives, such as department challenges or recognition for teams consistently applying labels correctly.
-
Use interactive simulations that include realistic document classification exercises, mock compliance audits, and hands-on scenarios where employees must correctly apply sensitivity labels to different types of data.
3. Establish Clear Governance and Enforcement
A well-defined governance structure ensures consistent labeling practices.
-
Assign data stewards to oversee the adoption process, ensure consistency in labeling practices, and serve as a point of contact for users with classification questions.
-
Conduct regular audits of labeled content, ideally on a quarterly or biannual basis, to ensure continuous compliance and identify areas for improvement.
-
Set up automated alerts for improperly classified sensitive data, prompting users to correct mislabeling.
-
Encourage peer accountability, where teams review each other’s label usage and share best practices.
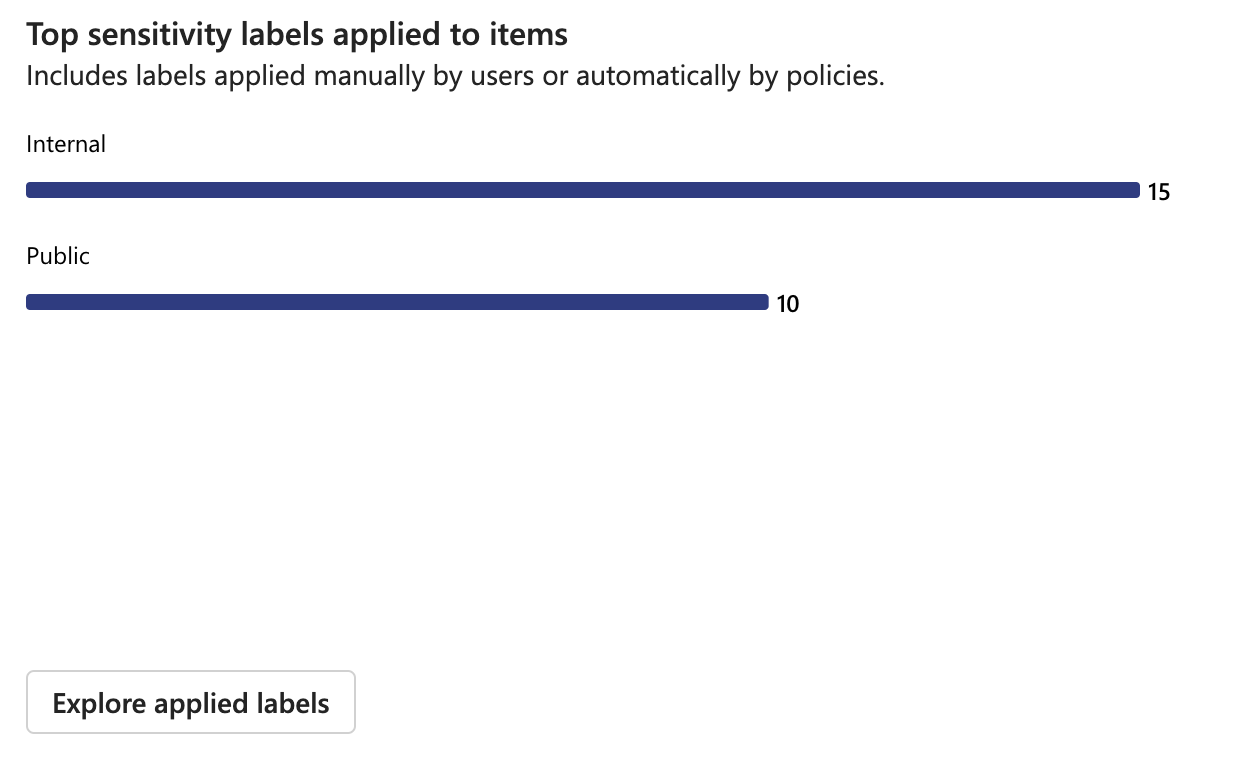
Measuring Adoption Success with Microsoft Purview
Tracking the adoption of sensitivity labels is crucial to ensuring their effectiveness and identifying areas for improvement. Microsoft Purview provides built-in reports that help organizations measure adoption success. Key metrics to track include:
-
Label Coverage: The percentage of documents and emails that have been labeled, helping assess overall adoption rates.
-
Label Usage Trends: Identifying which labels are used most frequently and whether they align with data classification policies.
-
User Engagement: Monitoring which departments and individuals are applying labels correctly and consistently.
-
Mislabeling and Overrides: Tracking instances where users override or incorrectly classify documents to identify training needs.
-
Data Protection Impact: Evaluating whether applying sensitivity labels has reduced incidents of data leaks or unauthorized access.
Organizations should review these reports regularly to adjust training programs, refine label policies, and ensure continuous improvement in sensitivity label adoption.

Conclusion: Building a Culture of Data Protection
Adopting sensitivity labels successfully requires more than just implementing policies—it requires a culture shift in how employees handle and classify information. Organizations that take a structured and user-focused approach will experience fewer data leaks, better regulatory compliance, and increased security confidence.
With the right strategy, sensitivity labels become an asset rather than a burden, empowering employees to protect data without disrupting productivity.
Other articles in this series
This is a blog post series that consists of multiple post. Here is an overview of all posts in this series:
- The importance of data security when deploying Copilot in your organization
- Building a sensitivity label strategy with Microsoft Purview: Protecting data in the era of Microsoft Copilot
- Adopting sensitivity labels to drive data security in the era of Microsoft Copilot
Stay tuned! More posts are coming!