Building a sensitivity labeling strategy with Microsoft Purview: Protecting data in the age of Copilot
Data security is no longer an afterthought—it’s a fundamental requirement in a world where AI-driven tools like Microsoft 365 Copilot are integrated into daily business processes. Sensitivity labels play a crucial role in governing access, ensuring compliance, preventing data leaks, and visually marking confidential content.
Microsoft Purview Information Protection allows organizations to classify and protect their data with sensitivity labels that define how information can be shared, accessed, and secured. Labels can automatically encrypt content, restrict access, prevent sharing, and even apply watermarks to clearly indicate document confidentiality. Watermarking is particularly useful in preventing accidental data leaks, as it visibly signals document sensitivity, reminding users to handle it with care.
This is especially important in the context of Copilot for Microsoft 365, as Copilot leverages organizational data to generate responses. Without proper labeling and protection, sensitive information could be exposed to unauthorized users, leading to compliance risks and data breaches. By automating classification and watermarking sensitive content, organizations can ensure that AI-generated outputs respect security policies and maintain trust in data handling.
Purview Information Protection: The Foundation for Securing Copilot
Microsoft Purview Information Protection (MPIP) provides a framework for classifying, labeling, and protecting data across Microsoft 365 applications and beyond. Sensitivity labels allow organizations to:
- Classify data based on confidentiality levels.
- Apply protection policies, such as encryption and access restrictions.
- Control external sharing and data loss prevention (DLP) measures.
- Monitor and audit label usage to track compliance.
For Copilot, Purview sensitivity labels ensure that AI-driven content generation adheres to organizational security policies. If a document is labeled “Confidential – Finance,” Copilot will respect this classification, ensuring that only authorized users can access related insights.
What labels should an organization consider?
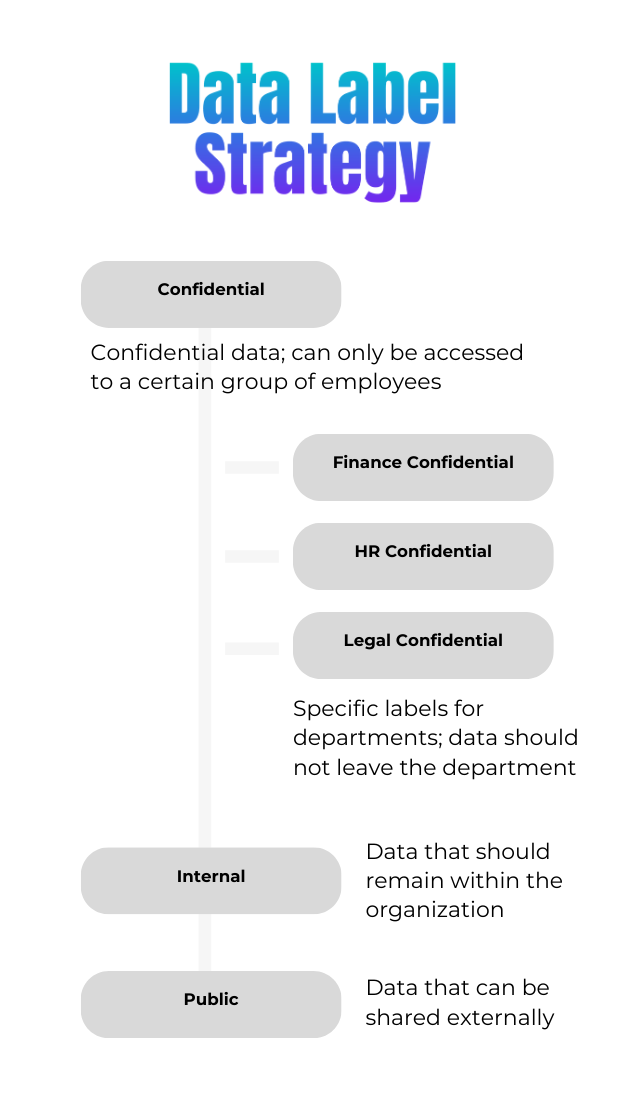
A well-structured labeling strategy starts with defining clear classification categories that align with business needs and regulatory requirements. Sensitivity labels should be broad enough to cover organization-wide security needs while also granular enough to protect department-specific data.
Common sensitivity label categories
While every organization is unique, a typical sensitivity labeling structure might include the following:
- Public – No restrictions, suitable for general use (e.g., marketing brochures, public announcements).
- Internal Use Only – Restricted to employees, prevents external sharing (e.g., internal policies, team updates).
- Confidential – Limited to specific teams, applies encryption (e.g., financial reports, budget plans).
- Highly Confidential – Strict access control with encryption, watermarking, and restricted external sharing (e.g., M&A documents, executive strategy plans).
- Restricted – Most sensitive data, accessible only to designated individuals or departments (e.g., legal contracts, board meeting minutes).
Department-specific sensitivity labels
Beyond broad organizational categories, departments often require specific sensitivity labels to protect data that should never leave their domain. Some examples include:
| Label Name | Department | Use Case | Protection Settings |
|---|---|---|---|
| HR Confidential | HR | Employee records, salary information, performance reviews | Restrict access to HR team only, prevent external sharing |
| Legal Privileged | Legal | Attorney-client privileged documents, contracts | Enforce encryption, restrict access to legal personnel |
| Finance Restricted | Finance | Financial statements, audit reports | Encryption, limited to finance department |
| R&D Confidential | Research & Development | Intellectual property, product designs | Block sharing outside R&D team, enforce watermarks |
| Executive Restricted | C-Suite & Board | CEO and board-level strategy, acquisitions | Restricted to named executives, strict access control |
Why department-specific labels matter
Department-based labels help ensure data does not accidentally leave a designated business unit, reducing security risks and improving compliance. For example:
- An “HR Confidential” label ensures that salary data, contracts, and employee performance reviews remain within the HR department.
- A “Legal Privileged” label ensures that only the legal team can access sensitive contracts, reducing the risk of exposure.
- A “Finance Restricted” label prevents budget documents and financial reports from being shared externally, helping with SOX and GDPR compliance.
Automating label assignment
Organizations can automate label assignment using Microsoft Purview’s machine learning and content inspection to detect sensitive content and apply the right label. For example:
- If an Excel file contains employee ID numbers or tax information, it can automatically receive the HR Confidential label.
- A document with legal disclaimers can be automatically tagged as Legal Privileged.
Combining labels with Copilot
Sensitivity labels also ensure Microsoft 365 Copilot respects data protection policies. For example:
- HR Confidential → Prevents Copilot from summarizing performance reviews in shared spaces.
- Legal Privileged → Blocks Copilot from extracting contract details into an email draft.
- Finance Restricted → Ensures Copilot doesn’t surface financial reports in general team meetings.
By combining broad and department-specific labels, organizations enhance data security, prevent leaks, and maintain compliance while enabling employees to work efficiently with Microsoft Purview and Copilot.
Who should have access to a certain label?
Not all users should be able to see, apply, or modify all sensitivity labels. Implementing role-based access control (RBAC) ensures that labels are applied correctly and prevents users from misclassifying or mishandling sensitive data
Defining access levels for sensitivity labels
Sensitivity labels should follow the principle of least privilege; meaning users and departments should only have access to the labels they need for their job function.
| Label Name | Who Can Apply? | Who Can Access? | Additional Controls |
|---|---|---|---|
| Public | All employees | Everyone | No restrictions |
| Internal Use Only | Employees & contractors | Employees only | External sharing blocked |
| Confidential – Finance | Finance managers, CFO office | Finance team, C-Suite | Encryption, Copilot VIEW allowed, EXTRACT blocked |
| Highly Confidential – M&A | M&A team, select executives | M&A team, CFO, CEO | Watermarking, Copilot blocked |
| HR Confidential | HR managers, legal team | HR department only | Strict internal access, Copilot blocked |
| Legal Privileged | Legal team, compliance officers | Legal team only | Encryption, watermarking, Copilot blocked |
| Executive Restricted | C-Suite, Board members | CEO, Board, authorized executives | Strict access control, no external sharing, Copilot blocked |
Role-based access considerations
- Standard Employees: Can apply Internal Use Only labels but cannot access Confidential or Highly Confidential documents.
- Department-Specific Teams:
- Finance team can apply Confidential – Finance labels but cannot override HR or Legal labels.
- HR team can apply HR Confidential but cannot access Finance or Legal data.
- Legal team can apply Legal Privileged but cannot modify Executive Restricted documents.
- Executives & C-Suite: Can view most confidential data but require explicit approval to access Highly Confidential or Executive Restricted data.
Example: Sensitivity labeling in a large organization
Sample company: Global Financial Corporation (GFC)
GFC is a multinational banking firm implementing Microsoft Purview Sensitivity Labels to secure sensitive financial data while leveraging Microsoft 365 Copilot to enhance productivity. The challenge is ensuring AI-driven insights comply with data security policies while allowing employees to work efficiently.
Sensitivity labels used in GFC
GFC has a combination of broad organizational labels and department-specific labels to enforce granular data protection policies.
| Label Name | Department/Scope | Use Case | Protection Settings | Copilot Permissions |
|---|---|---|---|---|
| Public | Organization-wide | Marketing materials, press releases | No restrictions | Copilot can fully use |
| Internal Use Only | Employees | Internal newsletters, company-wide updates | Block external sharing | Copilot can EXTRACT content |
| Confidential – Finance | Finance | Budget reports, tax documents | Encryption, Finance team only | Copilot can VIEW but not EXTRACT |
| Highly Confidential – M&A | M&A Team | Mergers & acquisitions strategy | Strict access control, watermarking, encryption | Copilot access blocked |
| HR Confidential | HR | Employee records, salary data, contracts | HR team only, no external sharing | Copilot access blocked |
| Legal Privileged | Legal | Contracts, litigation documents | Enforce encryption, Legal team only | Copilot access blocked |
| Executive Restricted | C-Suite & Board | CEO-level strategy, financial forecasts | Restricted to executives, encryption | Copilot access blocked |
Access & labeling policies in GFC
- Role-Based Access Control (RBAC):
- Finance team can apply Confidential – Finance labels but cannot override Highly Confidential – M&Alabels.
- HR team can apply HR Confidential but cannot access Finance data.
- Executives can view all Confidential labels but require explicit approval for Highly Confidential data.
- Automatic Labeling Policies:
- If a document contains employee salary data, it is automatically labeled HR Confidential.
- If a file includes legal disclaimers, it is assigned Legal Privileged protection.
- If AI detects the presence of M&A deal terms, it applies Highly Confidential – M&A restriction
How sensitivity labels control Copilot usage in GFC
Copilot follows label permissions to ensure that only appropriate data is processed, summarized, or extracted:
-
Public & Internal Data → Copilot Fully Accessible
- Copilot can retrieve, summarize, and generate content based on Internal Use Only documents.
-
Confidential Data → Limited Copilot Access
- VIEW permissions allow Copilot to read financial reports, but EXTRACT is disabled, preventing it from inserting financial figures into emails.
-
Highly Confidential & Restricted Data → Copilot Blocked
- Copilot cannot process, summarize, or extract data from files labeled Highly Confidential – M&A, HR Confidential, Legal Privileged, or Executive Restricted.
Practical example of Copilot interacting with labeled data
Scenario: A finance employee drafts a board meeting summary using Copilot for Word.
- Copilot can reference “Confidential – Finance” reports (VIEW allowed).
- Copilot cannot pull figures from Highly Confidential – M&A documents (EXTRACT denied).
- If the employee tries to insert an HR Confidential document, Copilot blocks access entirely.
Scenario: An HR manager asks Copilot to draft an email about upcoming promotions.
- If the document contains HR Confidential details (e.g., salary increases), Copilot refuses to include content.
- If the document is Internal Use Only, Copilot can summarize the non-sensitive parts.
Conclusion
As organizations increasingly adopt AI-driven tools like Microsoft 365 Copilot, the importance of sensitivity labelinghas never been greater. Data security and governance are no longer optional—they are fundamental to ensuring compliance, preventing leaks, and maintaining trust.
A well-defined sensitivity labeling strategy enables organizations to:
- Classify and protect data automatically across Microsoft 365 applications.
- Restrict access based on roles and departments, ensuring sensitive content stays where it belongs.
- Control how Microsoft 365 Copilot interacts with labeled data, preventing AI from surfacing confidential information in unauthorized contexts.
- Ensure compliance with regulations like GDPR, HIPAA, and ISO 27001 by applying encryption, access controls, and data loss prevention (DLP) policies.
Key takeaways
- Sensitivity labels do more than control access—they also enforce encryption, restrict sharing, and apply visual markers like watermarks to reinforce security.
- Department-specific labels, such as HR Confidential and Legal Privileged, help prevent sensitive data from leaving its intended domain.
- Microsoft 365 Copilot can only process labeled content if it has the correct permissions, making it essential to configure VIEW and EXTRACT settings appropriately.
- Automatic labeling policies in Microsoft Purview reduce human error, ensuring consistency in data protection.
By taking a proactive approach to sensitivity labeling, organizations can confidently leverage AI-powered productivity tools like Copilot while maintaining data security, regulatory compliance, and business integrity.
Now is the time to implement a structured sensitivity labeling strategy to safeguard your organization’s data and ensure AI-powered collaboration remains secure.
Other articles in this series
This is a blog post series that consists of multiple post. Here is an overview of all posts in this series:
- The importance of data security when deploying Copilot in your organization
- Building a sensitivity label strategy with Microsoft Purview: Protecting data in the era of Microsoft Copilot
- Adopting sensitivity labels to drive data security in the era of Microsoft Copilot
Stay tuned! More posts are coming!